Changelog
Follow up on the latest improvements and updates.
RSS
Set up periodic cleanings of your equipment. You can schedule to delete files in certain folders, when they have not been used for a period of time, this way you can free up disk space and keep computers running fast and smoothly!
No more need to worry about the WiFi being turned off and affecting the geolocation of your devices. With our new feature that automatically turns on the WiFi you will have the location of your computers as long as this option is activated. And don't worry about attacks, while the WiFi is on we prevent all possible attacks through this network.
Find out how the storage of your hard disks are now in the Storage Configuration tab. You will also be able to see the disk slots and their specific storage capacities. Prevent your disks from becoming full and therefore your computers slow!
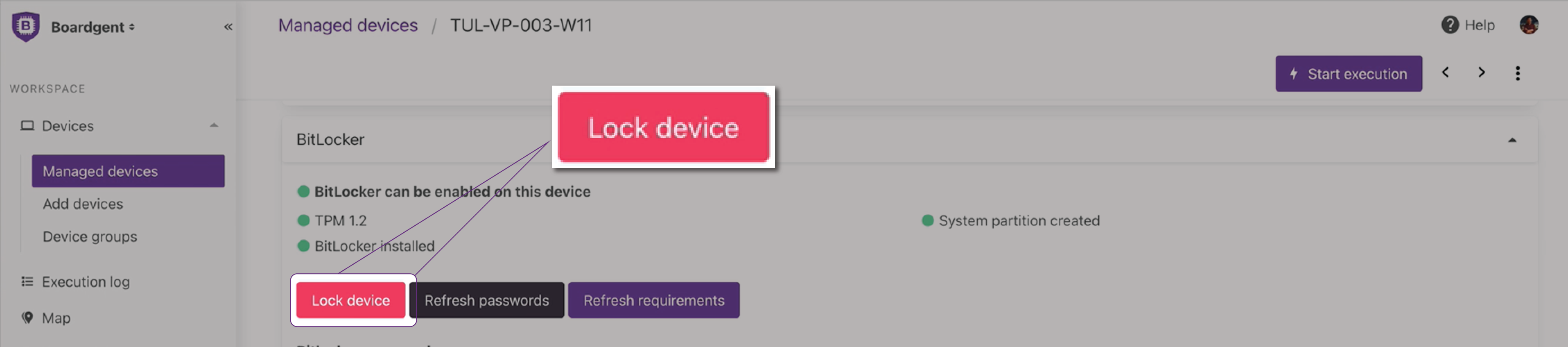
The new lock device option will allow you to lock any device you want at any given time. When the user turns on the computer with the locked disk, the device will ask for the recuperation key in order to be unlocked; these keys will only be found in the Boardgent console. Even if the disk is placed in another computer it will remain locked until the right key is typed. Your computers are safer than ever!
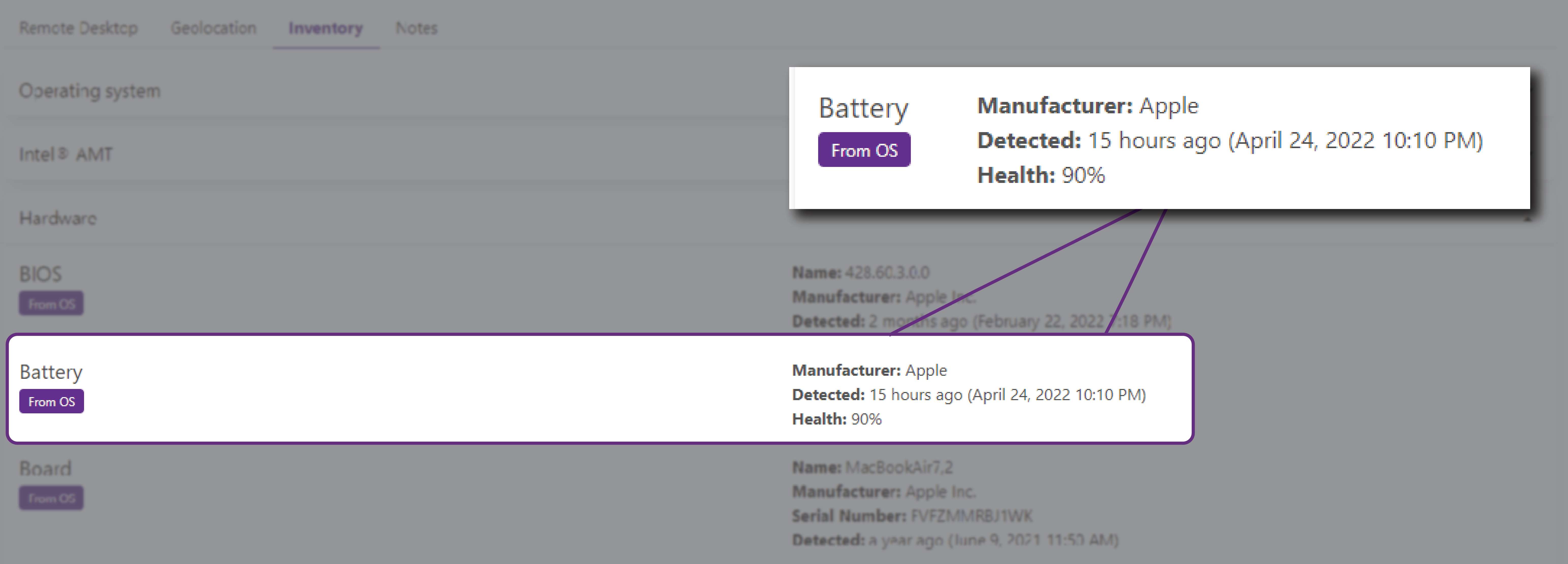
Find out the state-of-health of your batteries under the hardware inventory section to understand if the bad performance of your computers has to do with the battery degradation.
When you identify unauthorized access to your computers, someone reports a theft, or you need to dismiss an employee, remotely block access to the machine to prevent information leaks.
If you leave your Boardgent account open, don't worry. We close your session after minutes of inactivity.
Enable the automatic logout in roles' settings.
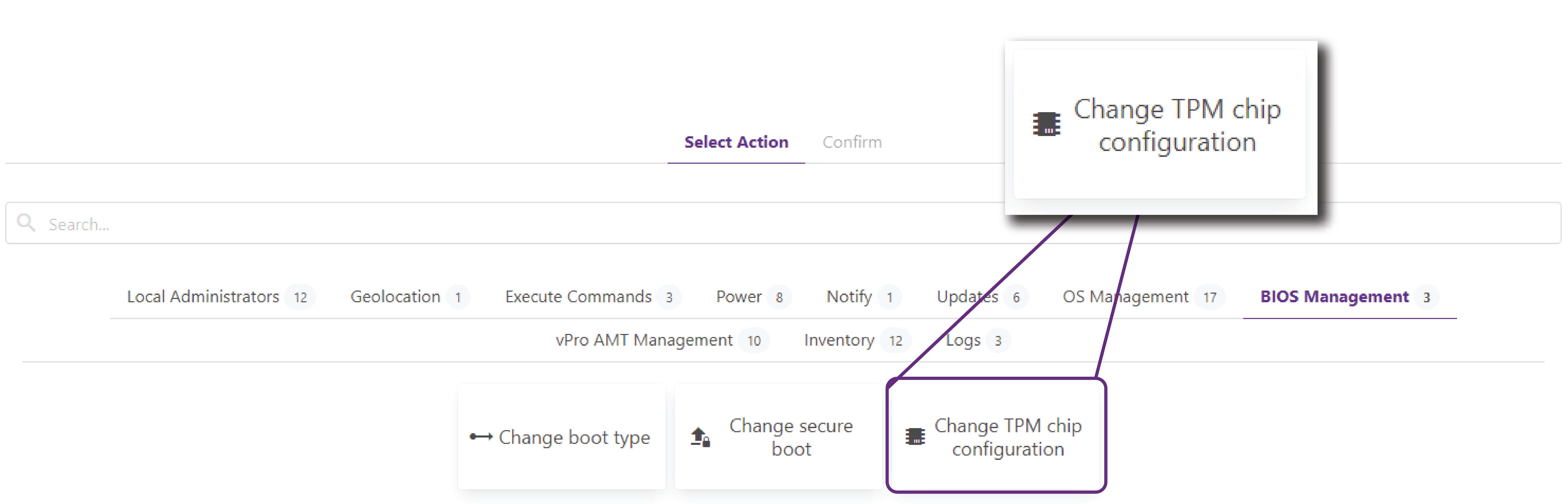
With Boardgent, you can remotely enable the TPM chip on your computers in minutes. Go to our executions section, and under the BIOS management tab, you’ll find the button called “Change TPM chip configuration.”
By default, Boardgent manages the password of the built-in administrator account. If you use another local account as the administrator, now you can configure it in the settings of the devices groups.
Load More
→